One Step Ahead! Fuji Electric's Fundamental Technologies
We provide an overview of our latest fundamental technologies that enhance our product development capabilities.
Security Technology for Embedded Devices
Wider use of IoT technology necessitates security measures for products
With IoT technology expanding on a global scale, our customers are also using the IoT in activities to improve productivity and quality through consolidation and analysis of information on production sites, optimizing energy utilization, and saving labor and power. On the other hand, having various devices connected to the Internet and other external environments has increased the risk of security accidents such as remote control by unauthorized access and information leakage caused by viruses. Such accidents can may cause damage to customers.
Given this, there is an increasing need to take security measures for products. In order to protect our products from unauthorized access, etc., we are working on developing technology to provide security features for CPUs embedded in electric and electronic devices that perform calculation and control (embedded devices).
Developing optimum technology suitable for security level and cost requirements
While enhanced security features reduce risks, they also lead to cost increases. However, safety cannot be ensured without a certain amount of cost. The key is to identify a good balance in the trade-off between features and cost.
We have previously developed a contactless IC card system (e-money reader) and acquired technology and expertise in security technologies such as data masking. Building up experience like this has enabled us to take the optimum security measures suitable for the security level and cost requirements of products, which is one of our strengths. We are currently focusing on the following as security technologies that are compatible with our main products, and moving ahead with R&D to install them in products.
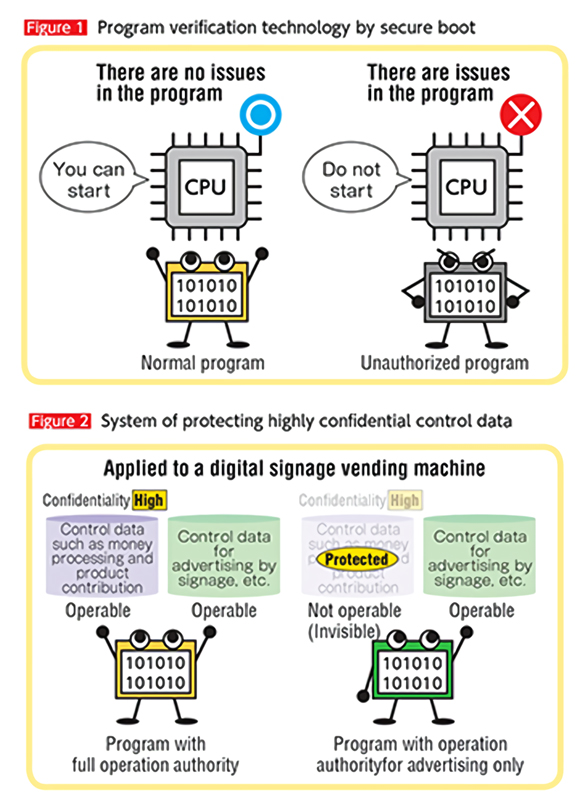
The foundation of these efforts is program verifi cation technology by secure boot.*1 If a program controlling products is subject to interference by unauthorized activity, the built-in CPU identifi es the activity and prevents the relevant program from starting, thereby preventing security accidents ( Figure 1 ). Even higher security is required if the product itself is connected to the Internet. By limiting the programs that are permitted to manipulate highly confi dential control data, we can protect such data from other programs to improve safety ( Figure 2 ).
In the future, we aim to provide this feature for power electronics equipment including PLCs*2 and HMIs,*3 digital signage vending machines, and automatic change dispensers.
-
*1
-
:The function of starting a product using only programs trusted by the manufacturer
-
*2
-
:Programmable Logic Controller
-
*3
-
:Human Machine Interface
Voices of developers

These days, more of our products are connected to the Internet and our responsibility for security is increasing. To start, we intend to equip our automatic change dispensers with a security feature and gradually increase the products to which it is applied. We will continue to work together with business groups on developing security technologies and contribute to the creation of products that customers can trust!
The article and the affiliations are at the time of coverage.
